ROP Emporium Ret2win (64 Bits) Writeup
Hello world. Ret2win is the first challenge in ROP Emporium. A fairly easy challenge where I had to call the ret2win() function. Before starting with the challenge, make sure your basics are strong. Do read my previous blogs for concepts. Let’s get started with the challenge.
Challenge
We do not get any source code for this challenge. First I had to start with the usual procedure of finding what type of file ret2win binary is.

Now I have to figure a way out to find the functions present in the binary ret2win. After finding the information on the functions using “info functions”, I found pwnme() and ret2win(). Pwnme() did not seem that interesting but ret2win() calls system()
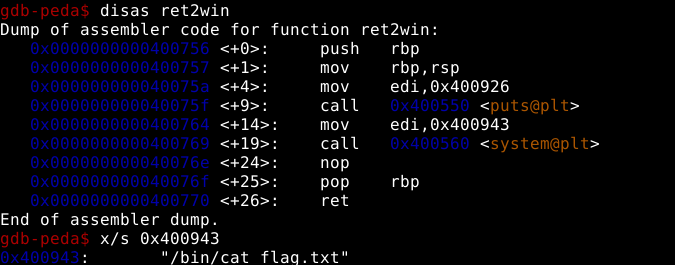
“0x400943” is copied to EDI. Using “x/s 0x400943” to find what it is. Calling this function will get us the flag. Also the address for ret2win() is “0x400756”
I tried to find the number of characters to overwrite the buffer, padding, and RBP with the trick I used in my previous blogs, But it failed here. So I had to go to the old method of creating a pattern and checking the offset value. For this I used pattern create 100.

I give the input in gdb to check how the stack and register information has changed.

We notice how the registers has changed here. RBP has been overwritten with “A)AAEAAa”. Now we could check the offset value with “pattern offset”.

Time to draw the stack diagram and find the number of characters required to overwrite Buffer, padding and RBP.

So I had to use 40 characters to overwrite the buffer, padding and RBP to use RIP for giving the ret2win() address. I used this exploit to get the flag.

Running this exploit should give us the flag.

WE HAVE OUR FLAG!
Hope you understood the challenge. Do check out my other blogs.
Don’t forget to give some claps if you reached here :) Follow me for more writeups.
Goodbye:)
